We Secure
What Matters.
With a team of passionate security experts by your side, we provide trustworthy strategies and fast response - so you can focus on growing your business, knowing you’re in good hands.
Protect Your Business Now
Security Comes First
Our experts deliver continuous protection and fast incident response so you can focus on growth. Trusted strategies, measurable results.
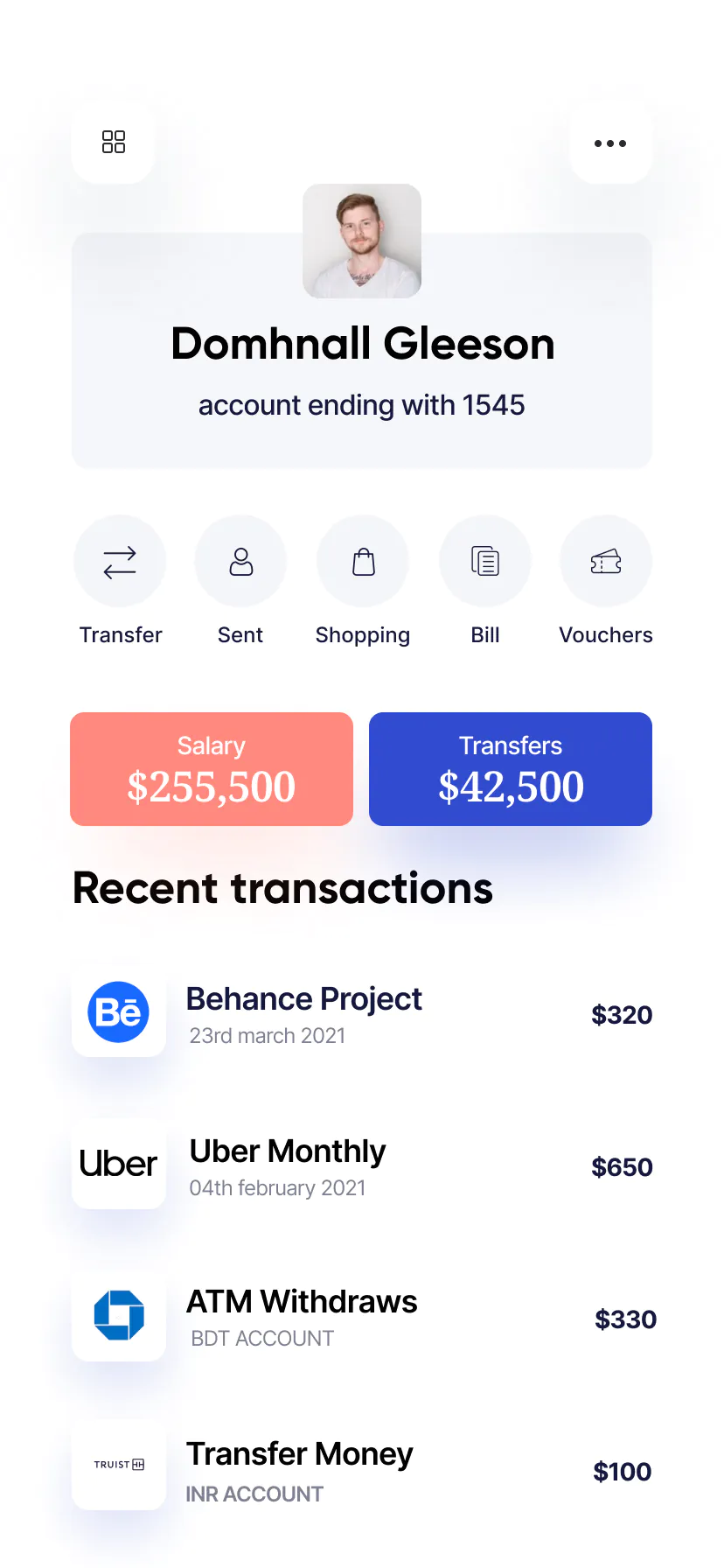
We Take Care of Your Business
End-to-end cybersecurity - from risk discovery to 24/7 monitoring and rapid response - tailored for enterprise needs.
Cybersecurity Matters
Proactive defenses, real-time detection, and expert response to keep your data and operations secure - always on, always ready.
KEEP SCROLLING FOR MORE
KEEP SCROLLING FOR MORE
.svg)
Cybersecurity Risks
How We Secure protects you and keeps you safe!
At We Secure, we excel in delivering robust cybersecurity solutions through a focused framework: Identify, Secure, Monitor, Respond. Our approach ensures that your organization is protected at every stage, minimizing risks and optimizing security.
1
Identify
We begin by understanding your business objectives and regulatory requirements to identify potential cyber threats and vulnerabilities. We develop personalized security strategies that align with your risk tolerance and compliance needs.
2
SECURE
Our team implements comprehensive security measures tailored to your specific environment. By building security into your systems, we fortify your defenses against cyber threats, ensuring data integrity and confidentiality.
3
MONITOR
Through 24/7 monitoring, we observe your network and systems continuously, identifying any suspicious activities or anomalies. Our proactive approach enables us to prevent potential breaches by addressing issues before they escalate.
4
RESPOND
In the event of a cyber incident, our rapid response team acts swiftly to neutralize the threat, minimize damage, and restore operations. Our incident response services ensure your business can return to normalcy with minimal disruption.
1
Identify
1
Identify
We begin by understanding your business objectives and regulatory requirements. This allows us to identify potential cyber threats and vulnerabilities. We develop personalized security strategies that align with your risk tolerance and compliance needs.
2
SECURE
2
Secure
Our team implements comprehensive security measures tailored to your specific environment. By building security into your systems, we fortify your defenses against cyber threats, ensuring data integrity and confidentiality.
3
MONITOR
3
Monitor
Through 24/7 monitoring, we observe your network and systems continuously, identifying any suspicious activities or anomalies. Our proactive approach enables us to prevent potential breaches by addressing issues before they escalate.
4
RESPOND
4
Respond
In the event of a cyber incident, our rapid response team acts swiftly to neutralize the threat, minimize damage, and restore operations. Our incident response services ensure your business can return to normalcy with minimal disruption.
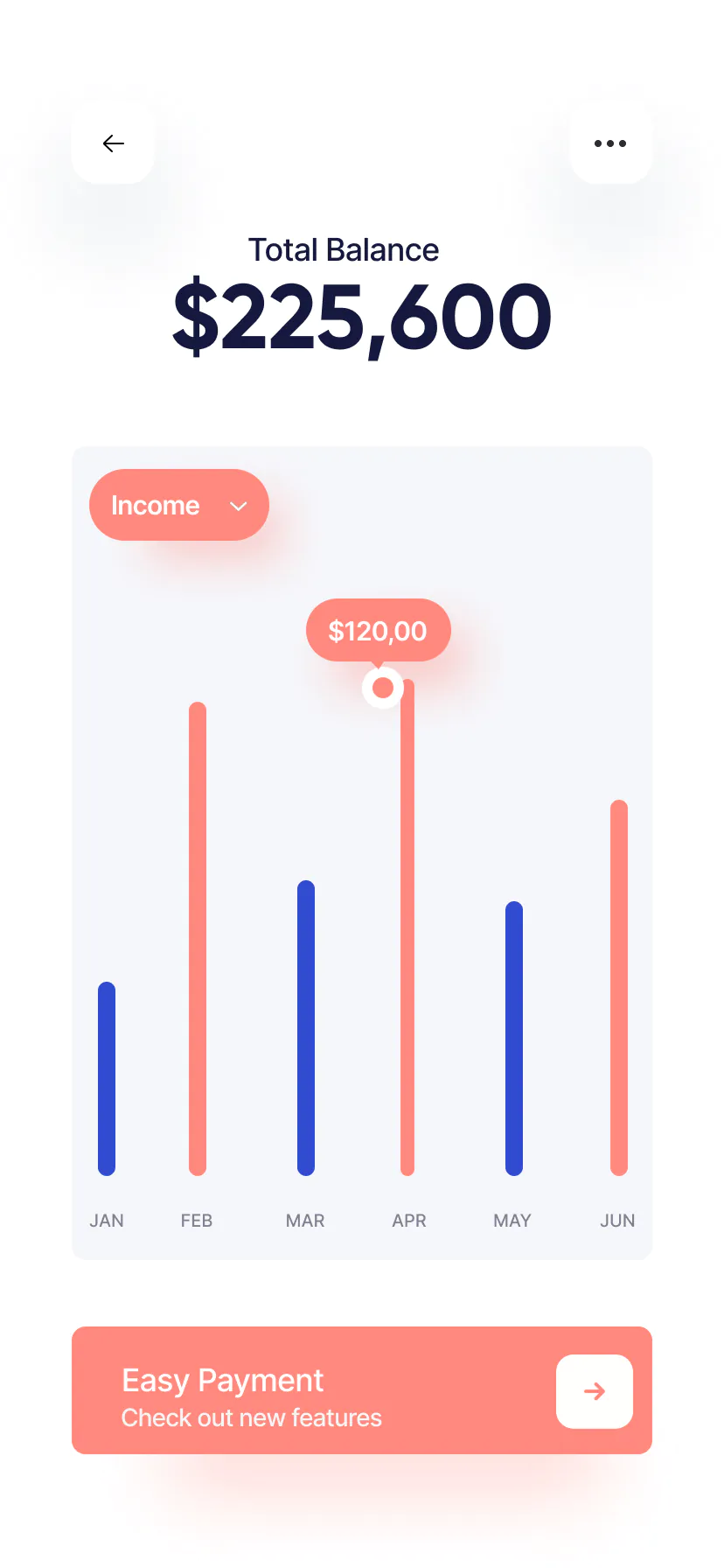
Key Security Insights 2024
Trends, data and actions
2024 breaches often involved compromised credentials.
Over a quarter caused by privilege misuse or stolen credentials.
Most SMB incidents used legitimate tools, not malware.
Data exfiltration occurred within 24 hours in ~42% of cases.
The Cost of Ransomware is Increasing YoY

Projected global cost of cybercrime in 2025
Estimated global economic impact of cybercrime in 2025.
$
12.000.000.000
Protect Your Business Now
Who is Behind
We Secure?
With more than 20 years of experience, We Secure has built a reputation as a cybersecurity company trusted by enterprises.
learn more about us





Our team combines deep knowledge of evolving threats with practical strategies that reduce risk and strengthen resilience.
As a top provider of enterprise cybersecurity solutions, we deliver managed services, incident response, and continuous security management to protect critical systems and support business growth.
As a top provider of enterprise cybersecurity solutions, we deliver managed services, incident response, and continuous security management to protect critical systems and support business growth.



We are a team of
Qualified Experts
learn more about us
Cybersecurity Experience and Expertise
Decades of success in enterprise cybersecurity, managing complex incidents and advanced threats.
Practical Data Security Solutions
From proactive protection to rapid response, our cybersecurity services are always focused on measurable results.
Trusted by Leading Companies
Proven record securing top institutions and enterprises with tailored cybersecurity solutions.
contact our team of experts
.svg)
Why Partner With
We Secure?
Choosing the right cybersecurity company is critical for protecting your business. Here’s why organizations trust We Secure as their long-term partner:
contact our team of experts
Discover We Secure’s
Services
Our broad range of cybersecurity services covers every aspect of enterprise cybersecurity - from managed protection and continuous monitoring to incident response and digital forensics. Each solution is designed to reduce risk, strengthen resilience, and keep your business secure.
Discover We Secure’s
Services
Our broad range of cybersecurity services covers every aspect of enterprise cybersecurity - from managed protection and continuous monitoring to incident response and digital forensics. Each solution is designed to reduce risk, strengthen resilience, and keep your business secure.
.svg)
MANAGED SECURITY & NETWORK SERVICES
Comprehensive managed cybersecurity services covering network protection, firewall management, and intrusion prevention. We keep your infrastructure secure through proactive monitoring and defense.
24/7 threat detection and response across endpoints, networks, and cloud
Integrated telemetry for fast attack detection and accurate alerts
Automated response workflows for quick incident handling
Proactive threat hunting to find hidden threats
Learn More
.svg)
.svg)
MANAGED DETECTION & RESPONSE
Advanced detection and response services designed to identify and neutralize threats across endpoints, networks, cloud, and applications. Real-time monitoring and proactive threat hunting minimize risks before they escalate.
Real-time monitoring and proactive threat hunting across endpoints, networks, and cloud
Advanced detection to identify and mitigate multi-vector attacks early
Rapid containment and automated response to minimize impact
Continuous visibility and threat intelligence integration for ongoing security improvement
Learn More
.svg)

INCIDENT RESPONSE & DIGITAL FORENSICS
Rapid incident response services to contain breaches, mitigate impact, and restore operations. Our digital forensics experts investigate root causes, helping prevent repeat incidents and strengthen defenses.
Rapid response to contain threats, minimize damage, and restore operations
In-depth digital forensics to determine incident scope, cause, and impact
Proactive readiness services including training, playbooks, and simulations
Continuous threat intelligence to enhance detection and prevention efforts
Learn More
.svg)

CLOUD SECURITY
Tailored cloud security solutions for Microsoft 365, CNAPP, and sensitive data. We protect cloud environments against misconfigurations, breaches, and compliance risks.
Full protection across Microsoft 365, multi-cloud, and hybrid environments
Automated posture management and policy enforcement
Strong identity, access, and data security
Ongoing assessments to ensure compliance and resilience
Learn More
.svg)

SECURITY ASSESSMENT SERVICES
Thorough security assessment services to uncover vulnerabilities before attackers do. From penetration testing and breach simulation to zero-trust evaluations, we help you build stronger defenses.
Comprehensive vulnerability assessments to identify hidden risks
Real-world breach simulations to test defenses and response readiness
Zero-trust maturity evaluations to improve access and identity security
Actionable insights and strategic roadmaps for strengthening security posture
Learn More
.svg)

SECURITY CONSULTING
Expert cybersecurity consulting focused on architecture design, compliance, and hardening. We align your security strategy with business goals and regulatory requirements.
Customized security architectures aligned with your business goals
Compliance strategies for NIS2, DORA, ISO 27001, and other frameworks
Practical hardening measures to reduce attack surfaces and increase resilience
Ongoing assessments and guidance to ensure sustained security posture and regulatory adherence
Learn More
.svg)
Discover We Secure’s
Services
Our broad range of cybersecurity services covers every aspect of enterprise cybersecurity - from managed protection and continuous monitoring to incident response and digital forensics. Each solution is designed to reduce risk, strengthen resilience, and keep your business secure.
Managed Security & network services
MANAGED DETECTION & RESPONSE
INCIDENT RESPONSE & DIGITAL FORENSICS
CLOUD SECURITY
SECURITY ASSESSMENT SERVICES
SECURITY CONSULTING
Our Security Ecosystem
We collaborate with leading technology providers and security vendors to deliver complete enterprise cybersecurity solutions. Our growing ecosystem ensures flexibility, scalability, and enterprise-grade protection.
learn more
60
+
Integrations
25
+
MSP & Channel Partners
15
+
Security Vendors
3,4
k
+
Attacks Prevented
learn more
Trusted by Leading Companies
We are proud to work with top companies across various industries. See what our clients say about us and how we’ve helped them stay secure.
.svg)
Start Securing Your Business Today.
Don’t wait until it’s too late. Protect your business with proven security solutions — let’s make it happen, now.
Contact our team and take the first step to a safer future.
.svg)





.svg)


















.svg)